Almost two years ago, when Microsoft announced that they were going to offer Defender for Business + Intune to all M365 Business Premium customers, I felt I had no choice – I had to deep-dive into this. I had been using ESET Protect for my customers (and I still do for my non-Microsoft customers!), but at the time, most of my customers were already on Business Premium.
I was impressed by what Microsoft had achieved in terms of cybersecurity, and over the next few months I migrated all my customers to Defender EDR.
One of the “revelations”, if you will, were the Attack Surface Reduction rules. If you – as a consultant or customer – are using the Microsoft EDR system and not leveraging ASR rules, why not? It is time to seriously consider using these.
What are Attack Surface Reduction Rules?
Attack Surface Reduction (ASR) rules are a set of policies that you can configure in Intune to make your endpoints much more secure and resistant to a cyberattack. They are designed to block common techniques that attackers use to mess with your devices, such as running nasty scripts, exploiting holes, or stealing passwords. By applying these rules, you can stop or limit the damage of many types of malware, ransomware, and phishing attacks.
How to Use ASR Rules in Intune?
To use ASR rules in Intune, you need to create a device configuration profile and assign it to your devices or groups. You can choose from 15 awesome rules that cover different scenarios, such as blocking executable files from email, preventing Office applications from spawning evil offspring, or disabling Win32 API calls from Office macros.
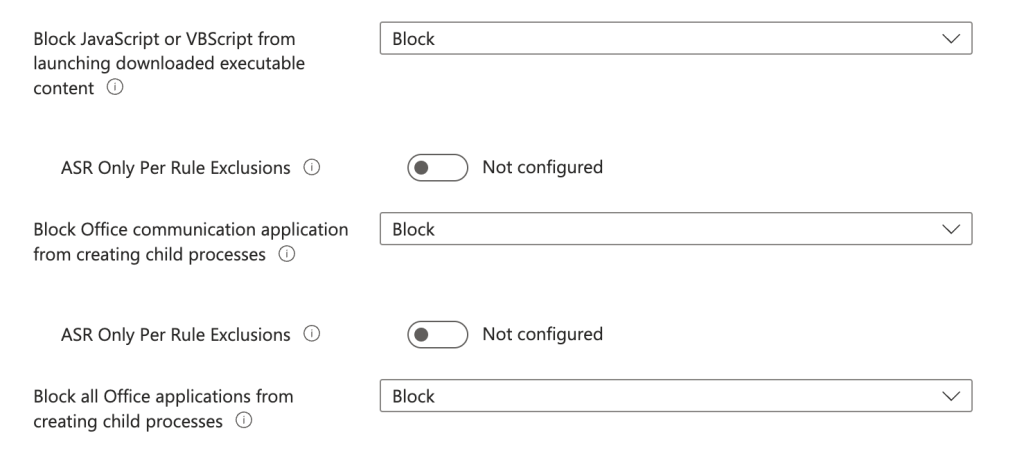
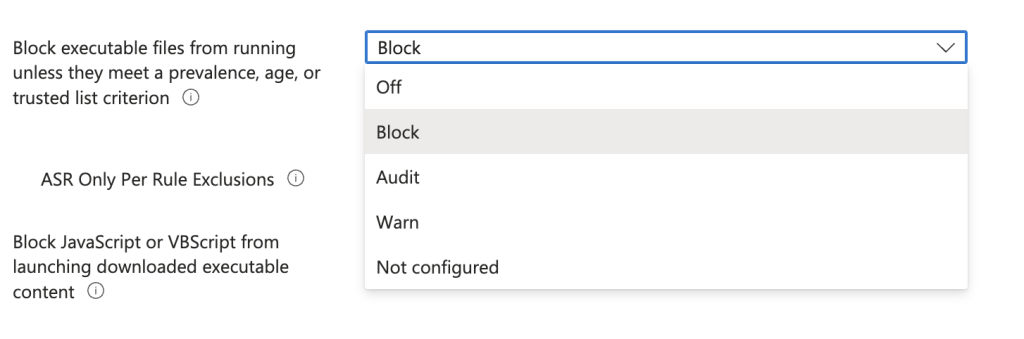
Before you apply the ASR rules to your devices, you may want to test them first and see how they affect your users and applications. Some of the rules may block legitimate actions or cause false positives, depending on your environment and use cases. For example, the rule to “Block executable files from running unless they meet a prevalence, age, or trusted list criterion” may interfere with developers compiling apps or users who use apps and utilities that are updated on a very frequent basis.
To avoid potential issues, it is wise to set some of the rules to “Audit” instead of “Block”, as this will allow the rules to run in the background and generate events without affecting the user experience.
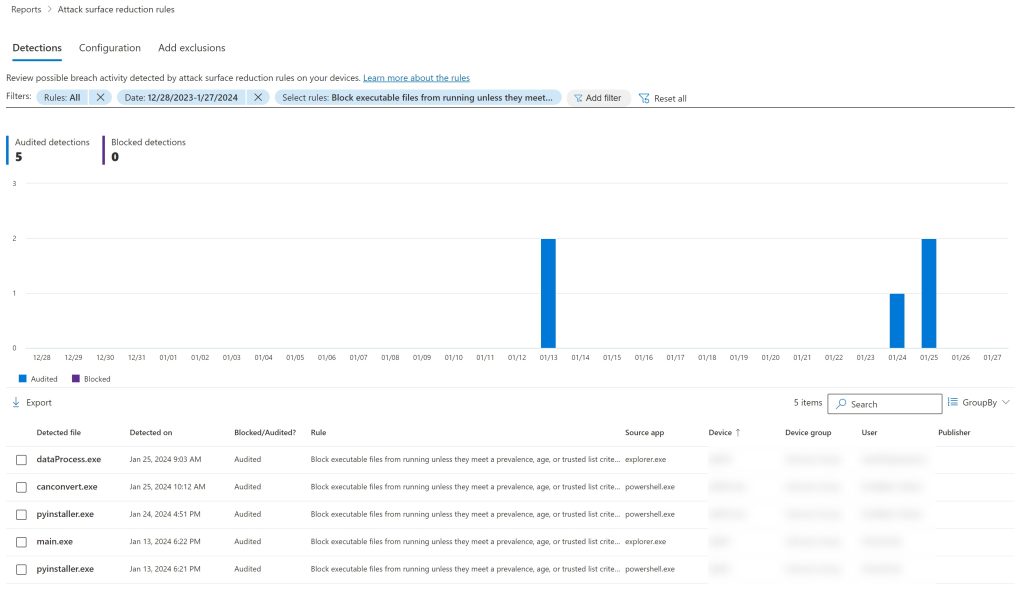
You can use the Report section of the Defender console to view any hits on the ASR rules and analyze their impact and frequency.
This way, you can fine-tune the rules and exclude any legitimate applications or paths before switching them to “Block” mode.
You can also tweak the rules to suit your needs, such as excluding certain applications or paths from the rules.
- To create a device configuration profile, go to the Intune portal and select Device configuration > Profiles > Create profile.
- Enter a name and description for the profile and select Windows 10 and later as the platform and Endpoint protection as the profile type.
- Under Endpoint protection, select Attack Surface Reduction and configure the rules that you want to apply. You can use the toggle switch to turn on or off each rule, and the settings icon to adjust the rule options.
- Click OK and then Save to create the profile.
- To assign the profile, go to the Intune portal and select Device configuration > Profiles > Select the profile > Assignments.
- Select the devices or groups that you want to apply the profile to and click Save.
Why Use Attack Surface Reduction Rules in Intune?
Using ASR rules in Intune can provide several benefits for improving your cybersecurity efforts, such as:
- Boosting the security posture of the endpoints by blocking or limiting common attack vectors.
- Lowering the risk of data breaches, ransomware infections, and financial losses.
- Improving the compliance with security standards and regulations.
- Making the management and deployment of the policies across the devices a breeze.
- Monitoring and reporting on the effectiveness and performance of the rules
If you want to protect your endpoints from threats, you should consider using ASR rules in Intune. They are a powerful and flexible tool that can work with your existing security solutions and provide an extra layer of defense.